Inventory for your data;create an inventory of your data to determine how data should be categorised and where it is stored. Categories might include critical, valuable, regulated, or proprietary. Once you have an inventory, you can determine how data needs to be protected and you can initiate data backup.
Ransomware Recovery
Ransomware Recovery Service
Infected with Ransomware? We can help to recover your
files within 24-48 hours in most cases.
Fast data recovery freeemergency ransomware evaluation will provide a quote to recover your files from a ransomware attack.
Please submit a request for a quote. It only takes 2 minutes to complete.
YES, we are able to help you recover your files from all types of Ransomware infections and have been successful with most types of ransomware attacks. All our work is guaranteed or your money back!
Our Ransomware Guarantee
Protect your company from a breach today. Because when ransomware hits, it hurts. Revenues plummet. Reputation suffers. In the worse cases, whole operations grind to a halt. SecOp Data Recovery is an established and trusted IT service provider worldwide. Our focus is to help clients recover from ransomware and provide cybersecurity to combat any future ransomware attacks.
We have the tools, knowledge and resources to guarantee the recovery of your data. We are available 24/7 for instant response. All recovery processes will begin immediately.
-
Recovery Guarantee
-
Ransomware Expoerts
-
Fast Data Recovery
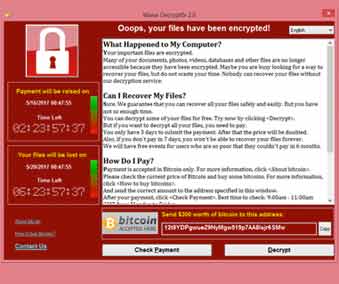
What Is a Ransomware Attack?
A ransomware attack is an attack carried out with malware that encrypts your systems and data. Attackers demand a ransom to decrypt your data, allowing you to access it again. Often, attackers ask for payment in cryptocurrency since it is anonymous and less traceable. The ransoms demanded can be minor or can be for large sums of money.
How to Prevent Ransomware: Building Your Ransomware Data Recovery Strategy
The most effective way to protect your systems against ransomware is to prevent it from being installed. The next best way is to anticipate how it can enter your systems and what data is likely to be targeted. This helps you focus protections and ensure that data is backed up before an attack.
To develop a robust data protection strategy, it's often easiest to start with your data and work from there. The following steps can help you develop a solid ransomware data recovery strategy.
-
-
Identify your endpoints; you need to know where your endpoints are to identify where ransomware infections might come from. Like with your data, you can categorise endpoints to determine priority and ensure high-value endpoints are protected appropriately.
-
Determine your recovery plan; create a ransomware data recovery plan for all assets and data, prioritizing mission-critical ones. You should be able to either restore or rebuild all assets, preferably from a master backup or image
-
Protect your backups; backups are only helpful when secure and accessible. You need to make sure your backups are as protected as your systems and data to ensure that you can restore data from backups and that the data you are restoring is reliable.
-
Duplicate data offsite; you should store at least one copy of data either offline, offsite, or both. This ensures that even if on-site backups are encrypted with ransomware you still can restore data. When storing these copies, make sure to secure data just as you would for the primary copy.

